Understanding Privacy Preference Policy Controls in macOS
It has been more than four years since Apple introduced new user data protections in the form of Privacy Preference Policy Controls (PPPCs) in the release of macOS Mojave. In 2018, this new way of working presented new challenges for IT admins and developers alike.
Since then, more IT admins than ever have looked to MDM solutions to manage these preferences within Apple’s framework to leverage a seamless experience when onboarding computers and deploying applications. I would like to explore the lessons I have learned from PPPCs, provide some troubleshooting tips and share my experience of using Privacy Controls to fix a system-wide problem.
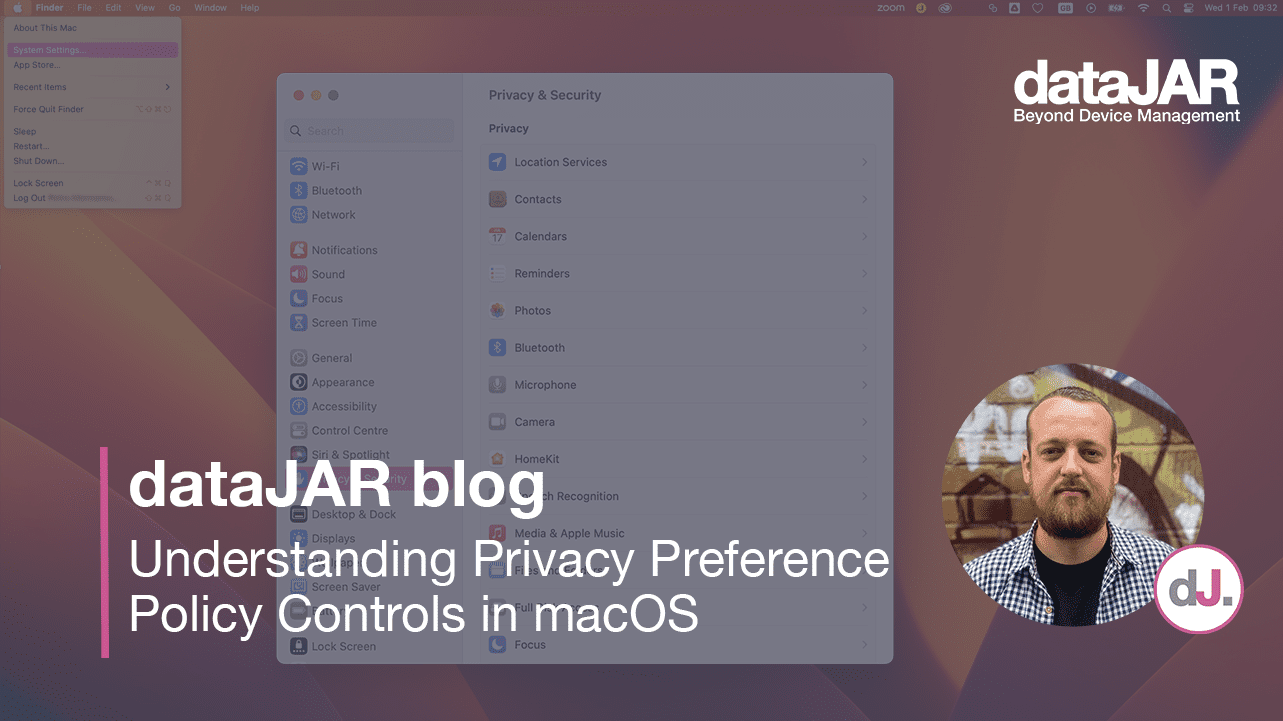
What is PPPC? Privacy Preference Policy Controls are payloads that can be deployed via MDM to control preferences for applications. The Privacy Preferences payload controls the settings that are displayed in the ‘Privacy’ tab of the ‘Security & Privacy’ pane in System Settings.
Please note, this behaviour can change between macOS versions, most notably in the upgrade to Big Sur from Catalina. Previously, any local user (either standard or admin) could approve screen capture and input monitoring PPPC requests. However, from the release of macOS Big Sur onwards, users have to click the padlock symbol in the bottom left corner of the screen in System Preferences and enter administrator login details to authenticate the change. PPPC Profiles mitigate this by either allowing, denying or letting standard users approve the desired preference.
Here are some examples of preferences that can be changed and the control options accordingly. To protect user privacy, Apple has not made some preferences configurable to ‘Allow’, such as the camera functionality. Some preferences – for example, screen recording – cannot be enabled by MDM, but we can change this permission so standard users can change the setting without local administrator privileges.
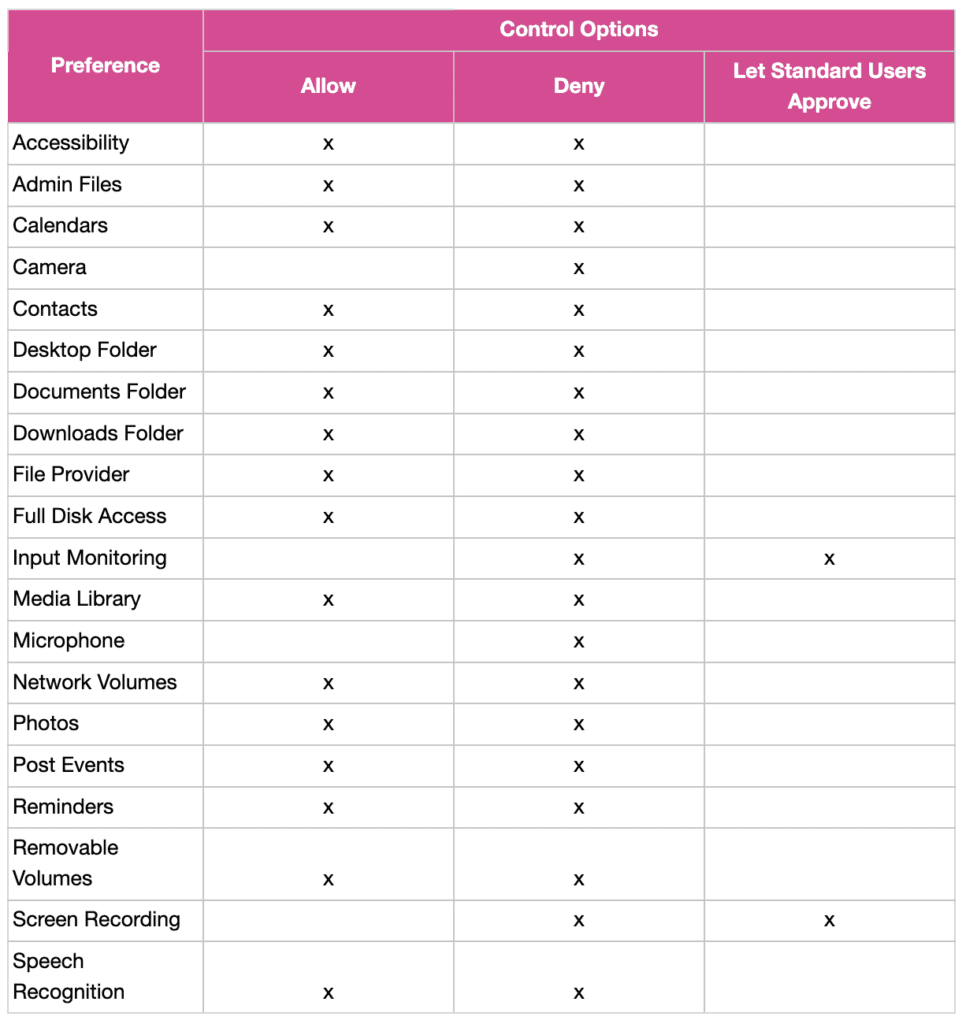
This protection on preferences empowers organisations to control applications on a more granular level to protect enterprise security. A popular tool among Mac administrators is PPPC Utility, due to its clean design and the way profiles can be uploaded directly to a Jamf Pro server; this is great for creating configuration profiles to manage your PPPCs.
Controlling these preferences is powerful but what options are available when the setting appears to stop working?
Introducing tccutil
This command line tool can reset system privacy permissions for macOS apps. The tccutil command manages the privacy database, which stores decisions the user has made about whether apps may access personal data. These settings are currently stored in an SQLite database located at /Library/Application Support/com.apple.TCC/TCC.db
This tool can be useful as, sometimes, the record for permissions can become stale or broken. You can reset the individual permissions or reset all permissions for any application installed.
Please remember to disable any active MDM PPPC policies before using this tool, or the setting may not be reset. Here are some examples of permissions that can be reset:
Unset
Accessibility
AddressBook
All
AlwaysAllowedService.AppleEvents
AppleEvents
BluetoothAlways
BluetoothPeripheral
BluetoothWhileInUse
Calendar
Calls
Camera
ContactsFull
ContactsLimited
DeveloperTool
ExposureNotification
ExposureNotificationRegion
FaceID
Facebook
FallDetection
FileProviderDomain
FileProviderPresence
FocusStatus
GameCenterFriends
KeyboardNetwork
LinkedIn
ListenEvent
Liverpool
MSO
MediaLibrary
Microphone
Motion
NearbyInteraction
Photos
PhotosAdd
PostEvent
Prototype3Rights
Prototype4Rights
Reminders
ScreenCapture
SensorKitAmbientLightSensor
SensorKitBedSensing
SensorKitBedSensingWriting
SensorKitDeviceUsage
SensorKitElevation
SensorKitFacialMetrics
SensorKitForegroundAppCategory
SensorKitKeyboardMetrics
SensorKitLocationMetrics
SensorKitMessageUsage
SensorKitMotion
SensorKitMotionHeartRate
SensorKitOdometer
SensorKitPedometer
SensorKitPhoneUsage
SensorKitSoundDetection
SensorKitSpeechMetrics
SensorKitStrideCalibration
SensorKitWatchAmbientLightSensor
SensorKitWatchFallStats
SensorKitWatchForegroundAppCategory
SensorKitWatchHeartRate
SensorKitWatchMotion
SensorKitWatchOnWristState
SensorKitWatchPedometer
ShareKit
SensorKitWatchSpeechMetrics
SinaWeibo
Siri
SpeechRecognition
SystemPolicyAllFiles
SystemPolicyDesktopFolder
SystemPolicyDeveloperFiles
SystemPolicyDocumentsFolder
SystemPolicyDownloadsFolder
SystemPolicyNetworkVolumes
SystemPolicyRemovableVolumes
SystemPolicySysAdminFiles
TencentWeibo
Twitter
Ubiquity
UserAvailability
UserTracking
WebKitIntelligentTrackingPrevention
Willow
When resetting a permission, you need to identify the application in your command via the application bundle identifier. You can find this using the below command:
Unset
lsappinfo info -only bundleid “Google Chrome”
To reset the Screen Recording permission for Google Chrome, you would use:
Unset
sudo tccutil reset ScreenCapture com.google.Chrome
To reset Screen Recording permission for all apps, you would use:
Unset
sudo tccutil reset ScreenCapture
To reset all permissions for Google Chrome, you would use:
Unset
sudo tccutil reset All com.google.Chrome
To reset all permissions for all apps, you would use:
Unset
sudo tccutil reset All
To give an example, this tool was helpful for me to use in early 2022 when I was remedying a known issue with Google Chrome version 99.0.4844.74. Essentially, users would experience no change in functionality when enabling screen recording for the app. Below is the documentation of this issue from the developer notes at the time:
Unset
Bug: 1307502
If Chrome 97 or earlier was used to screen share a stale designated requirement may be cached in the system TCC.db. This stale record can cause issues starting with Chrome 98.0.4758.132 (extended stable), 99.0.4844.74 (stable), 100.0.4896.45 (beta), 101.0.4929.5 (dev), 01.0.4933.0 (canary). These are the first releases to be signed with the new Developer ID certificate (https://crbug.com/1263152).
This CL will attempt to purge stale or thought to be stale screen capture records at early startup on macOS 10.15+. See
https://crbug.com/1307502#c11 for more details.
Without the TCC reset, the checkbox in System Preferences:Security & Privacy:Privacy:Screen Recording is wrong—it will show Chrome as approved (checked checkbox) based on its bundle ID, but contemporary Chromes will not match the saved designated requirement. Users looking at the checked checkbox will see that they’ve given Chrome access, but the system will not actually allow it access. The TCC reset revokes Chrome’s permission based on bundle ID, so the next attempt to access the screen will be treated the same as the initial attempt in a fresh installation. The system will create a new entry with the updated designated requirement on first access, the user will see an unchecked checkbox, and by checking it, will grant Chrome access, which the system will respect.
This doesn’t carry existing screen recording permission granted to archaic Chromes forward to modern Chromes, but it does make it so that the established UI flow for inspecting and granting permission works as intended and tracks reality.
I used tccutil to reset the privacy controls and deleted the PurgedStale records. Following this, I used the following commands on all devices affected and the issue was resolved:
Unset
Killall “Google Chrome”
Unset
tccutil reset ScreenCapture com.google.Chrome
Unset
defaults delete com.google.Chrome
PurgeStaleScreenCapturePermissionSuccessEarly2022Success
Unset
defaults delete com.google.Chrome
PurgeStaleScreenCapturePermissionSuccessEarly2022Attempts
Summary
Managing PPPCs has been challenging for some IT teams, but it is important to remember this change was made to enhance user privacy and to provide a framework for engineers to work in when managing privacy-sensitive features, such as the camera. It also empowers IT teams to drill in on their security posture because it raises valuable discussions about what should be allowed in the organisation on a per-app basis.
We work with our datajar.mobi customers to ensure PPPCs are used as effectively as possible in each organisation. We also have a library of PPPCs available for customers to benefit from, so please get in touch if we can offer assistance with this.