Apple’s single sign-on extension for macOS

History
Historically, macOS has had a number of solutions in providing single sign-on (SSO) for users to access an organisation’s services.
These have included:
- Apple’s Active Directory plug-in to allow a Mac to be permanently bound to an on-premise Active Directory Domain. This is used quite extensively in schools to allow students to log into a Mac with their Active Directory credentials.
- Apple’s Enterprise Connect application to allow Mac users to get single sign-on to services with Kerberos ticket-granting ticket (TGT) from local on-premise Active Directory Domains.
- Third-party applications including NoMAD and JAMF Connect which build on the functionality of Enterprise Connect.
Introducing Apple’s SSO extension
With the release of macOS 10.15, iOS 13 and iPadOS, Apple has added a new framework to allow developers to more easily supply solutions for SSO.
In macOS 10.15, Apple also added its own SSO extension for on-premise Active Directory Domains. This effectively replaces its Enterprise Connect product.
The Kerberos extension offers the following functionality:
- Allows local Mac users to acquire a Kerberos ticket-granting ticket (TGT) so they can seamlessly access services such as web services, file services and applications.
- Allows the user to change their Active Directory password, be notified when the password is close to expiring and change their local Mac password so it matches their Active Directory password.
- Use third-party scripts or apps to perform tasks based on state changes with the SSO extension.
Requirements
The Kerberos SSO extensions requires the following:
- macOS 10.15 or higher
- An on-premise Windows 2008 or higher Active Directory domain.
- The domain can be accessed via Wi-Fi, Ethernet or over VPN
- The devices must be managed by a Mobile Device Management (MDM) solution, such as datajar.mobi
Configuration
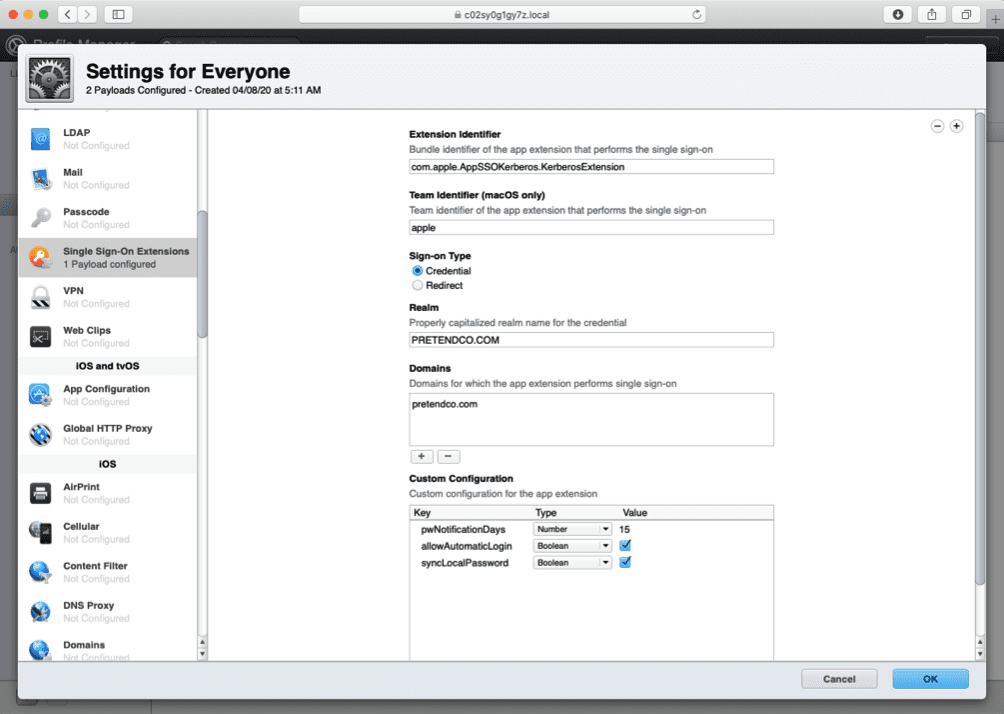
In order to configure the Kerberos SSO extension, an MDM must be used to deliver a configuration payload.
Here is an example payload that is used to configure the Kerberos realm plus additional options for passwords. This would be delivered to the Mac via your chosen MDM solution.
User Setup – macOS
From the user’s point of view, they will have to authenticate with their AD credentials once the Kerberos SSO extension has been configured.
This can be triggered a number of ways:
- If the Mac is connected to the network where the Active Directory Domain is available, they will be prompted to authenticate.
- If the user visits a web page that accepts Kerebros authentication or an app that requires it, they will be prompted.
- The user can choose to sign in the menu extra
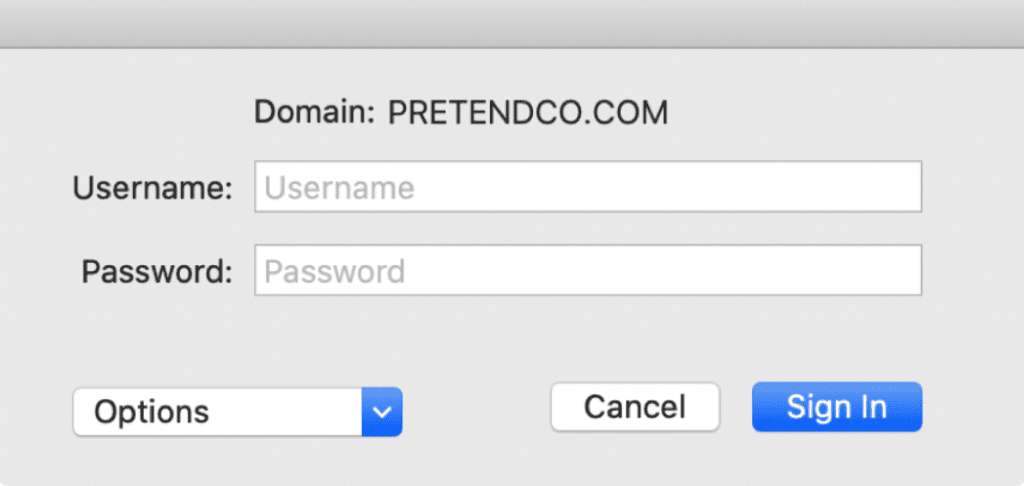
- The user can also choose to change their password. A password expiry notification can also be set to remind the user when they need to change their password.
Other macOS Features
The Kerberos SSO extension offers live password testing to make sure the password meets the requirements set by the Active Directory administrator.
To use this feature, you must be using the standard Active Directory password policies.
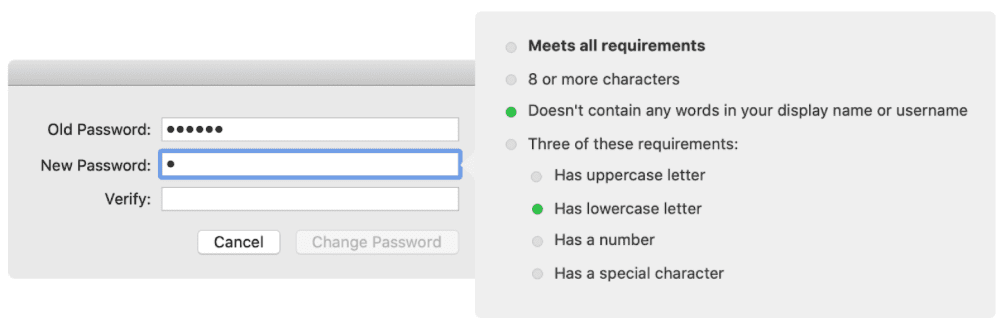
Instead of changing the password via the Kerbero SSO extension, the user can instead be redirected to a password change website.
The Kerberos SSO extension can be used to sync their local account password with the Active Directory password.
Smart Card support is available for cards that support Apple’s CrypoTokenkit APIs.
Custom scripts or applications can be used to respond to notifications from the Kerbero SSO extension. For instance, you could write a script that responds to the user authenticating, by mounting some sharepoints.
Summary
Even though this is just the first version, it offers some intriguing possibilities going forward.
Apple offers a full set of APIs to allow third-party developers to write their own SSO extensions. Hopefully, soon we will see examples from the likes of Microsoft, Okta etc.
Apple also offers a Kerberos extension for iOS allowing for SSO for apps and websites.
For further reading, these KB articles are worth a look.
Apple Kerberos SSO Extension User Guide.